Your Computer is Not Infected
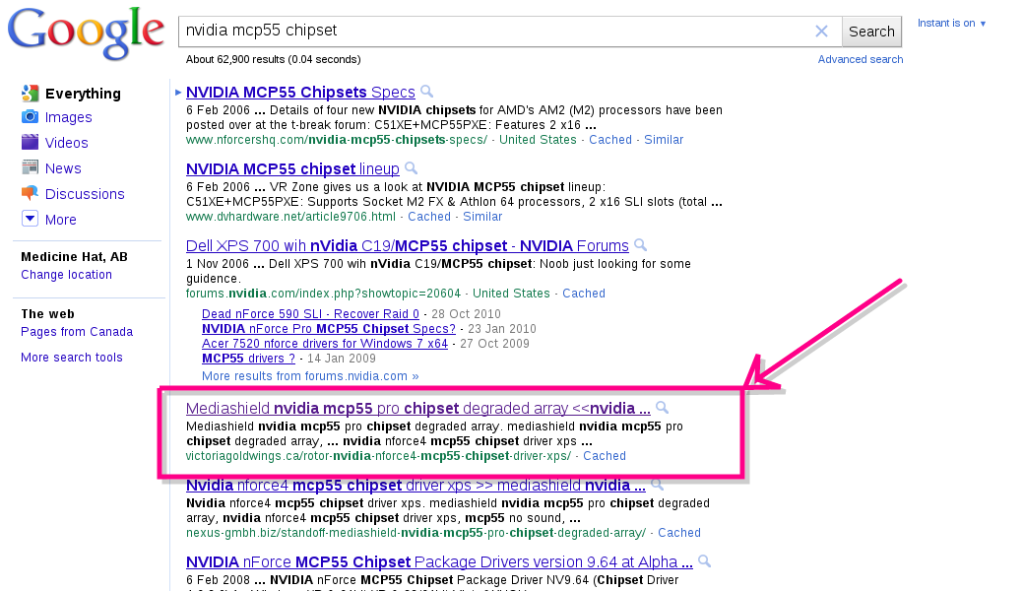
This is starting to get tedious. These companies trying to sell you their fake windows repair software by spoofing a message on your computer screen. The tactic is to scare you into loading their software which then infects your computer and requires you to pay a ransom to have it removed. Here is an example with screen shots of what I am talking about. I am searching google and the results come back with the following hits. Most of us have come to expect this when searching for virus or malware removal software but today it was for a raid chipset. I think google is in big trouble when esoteric searches like this one come back with phishing sites and it shows just how corrupted their database has become recently.
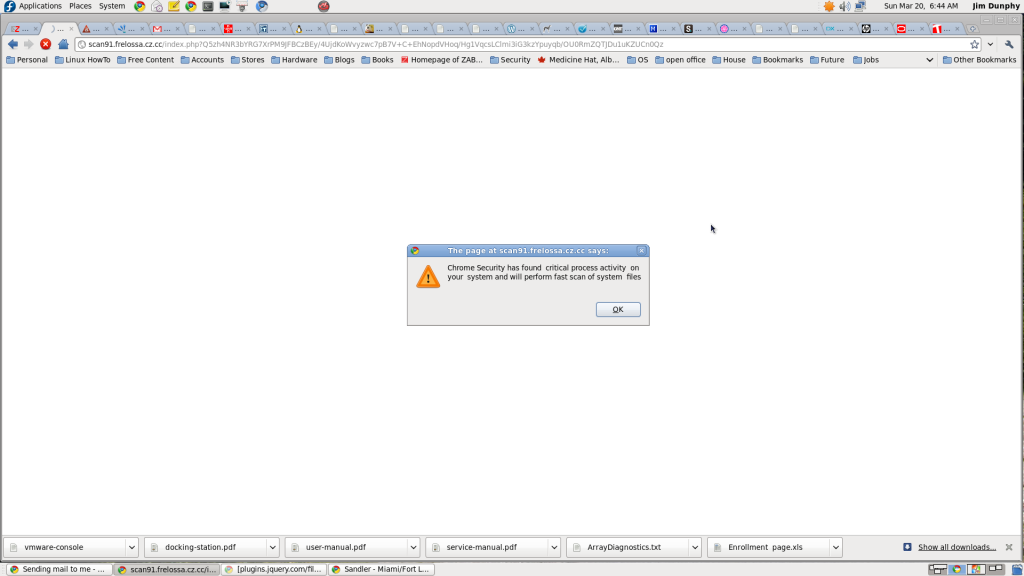
I click the link which I highlighted on the search results page above and up pops this official looking message dialog. It is attempting to pretend that it is coming from my browser and my computer. Google Chrome is really good about displaying the site where the message originates from and if you look carefully you can see the name of the site that is displaying this dialog box in the blue title bar.
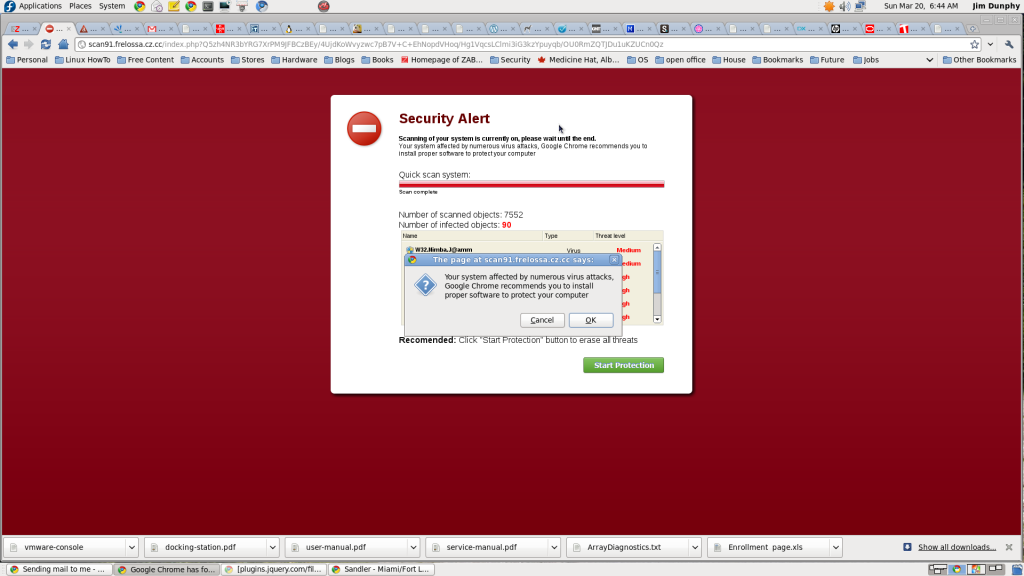
I dismiss this dialog box which by the way has complete modal control of my browser – meaning nothing else will work in this browser window until I acknowledge this and exit the pop up. The next page is a little javascript page that is displaying files on your computer just like you would normally see when doing a scan of your disk. it is running and finding all these infections in my computer. Here is a snapshot of that page during the run. A couple of odd things. First, they want to you click start protection even though it is still running. Most real software, that button would be disabled until the program finished. The second odd thing is the message that google chrome recommending this. It is just a browser and doesn’t know anything about my computer. Lastly, I don’t have any of those files on my computer. I run linux and those are windows files that are scrolling by.
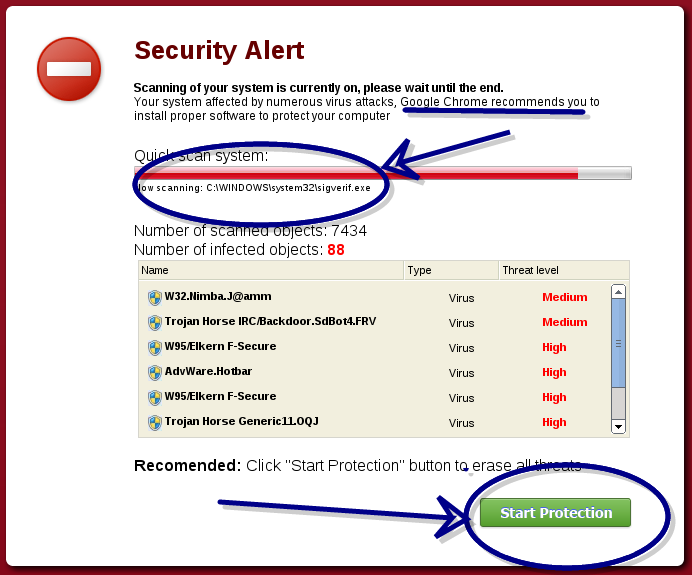
Now you have to love this. I am running linux and it telling me that my windows computer is infected. Just click on the link and they will take care of everything for me. Here is a warning for my friends and family. If you click that button on your windows computer, it would install itself and then infect your computer. I can not say this any stronger. Your computer is not infected. This is a fake message. This screen continues to run and then the following modal dialog window pops up explaining that things are very bad indeed with their recommendation that I should wait no longer and install the repair software now. Here is the last screen.
How do I protect myself from this?
- Install chrome browser and never use Internet Explorer unless you must
- Install chrome extension WOT (web of trust). It will provide an indicator on the search results
Note: Firefox, and other browsers. They all work fine but I recommend what I use and trust. Software is about trust. It takes time to earn your trust. If you have great results with Internet Explorer then that is your goto package. For me it is Chrome. It was Firefox in the past but now I like Chrome and the combination of speed in addition to some extra security checks. The version of Chrome I am running here is a nightly build of the developers tree and not appropriate to anyone other than programmers but I have my kids and my mother running chrome. They have never been tricked or installed malware thus far.
Lastly, it wouldn’t be any fun without explaining the code so here is some interesting parts.
<table>
<tbody>
<tr>
<td><textarea style="display:none" id="paths"></td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\explorer.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\hh.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\NOTEPAD.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\regedit.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\ST5UNST.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\TASKMAN.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\twunk_16.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\twunk_32.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\unvise32.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\winhelp.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\winhlp32.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\assembly\GAC_MSIL\CCC\2.0.0.0__90ba9c70f846762e\CCC.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\assembly\GAC_MSIL\CLI\2.0.0.0__90ba9c70f846762e\CLI.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\assembly\GAC_MSIL\LOG\2.0.2758.37155__90ba9c70f846762e\LOG.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\assembly\GAC_MSIL\MOM\2.0.0.0__90ba9c70f846762e\MOM.EXE</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\assembly\NativeImages_v2.0.50727_32\dfsvc\f985c62094467349a3fdcef8432fe412\dfsvc.ni.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Help\Tours\mmTour\tour.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\inf\unregmp2.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{0C3345A6-2671-4D4D-E866-8035399579B7}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{10FEEFBE-E1F7-166E-06D1-FD95B1F8D11B}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{159EFA33-202B-177B-C9BB-918AA78E4455}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{16859FDE-E9A7-FCC1-7749-8B0129FF2EC4}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{18792CA5-34C8-AFAF-91AE-B3E810BDA1DD}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{20029520-0281-991E-A9A7-778B9ED13330}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{236BB7C4-4419-42FD-0409-1E257A25E34D}\NewShortcut1_236BB7C4441942FD04091E257A25E34D.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{278A9FF6-F7E2-DEBF-BF9E-EA224C82847F}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2AE624B6-52A1-766B-5376-927F364DDC9E}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2C03FD7C-28A9-BD35-673F-64B988F93A12}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2D95950E-6D76-43E7-94A5-D9DBA2FD29E4}\ACDSeeDesktopShortcu_F99F74B4972B4B06B8936B3B0DB0128B.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2D95950E-6D76-43E7-94A5-D9DBA2FD29E4}\ACDSeePMShortcut_F99F74B4972B4B06B8936B3B0DB0128B.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2D95950E-6D76-43E7-94A5-D9DBA2FD29E4}\ACDSeeShowroomShor_89621A33AFFC45029C8C9D5A4EA9D15A.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2D95950E-6D76-43E7-94A5-D9DBA2FD29E4}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2D95950E-6D76-43E7-94A5-D9DBA2FD29E4}\DevDetectPMShortcut_ECE0113B23D04DD889E6D2F026CABF03.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2EC484F7-C770-C881-F6CA-358195A24D3A}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2F1E63CF-1595-9EDA-049C-FBC98265F73A}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{2F545934-B8AA-08A2-E844-1B3E43CDABB1}\ARPPRODUCTICON.exe</td>
</tr>
<tr>
<td></td>
<td>C:\WINDOWS\Installer\{350C9419-3D7C-4EE8-BAA9-00BCB3D54227}\places.exe</td>
</tr>
</tbody>
</table>
The code is pretty interesting as it uses XUL to force some of those pop up windows and override the mouse event handlers. The list above is huge. There were a few thousand entries that are displayed to the user like it is doing a scan and finally the same hard coded infected messages from this area of the code.
<table> <tbody> <tr> <td><table cellpadding="3" cellspacing="3" width="100%" border="0"></td> </tr> <tr> <td></td> <td><tr id="vir1" style="display:none;"></td> </tr> <tr> <td></td> <td><td width="65%"><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>W32.Nimba.J@amm</b></td></td> </tr> <tr> <td></td> <td><td width="20%">Virus</td></td> </tr> <tr> <td></td> <td></td> </tr> <tr> <td></td> <td><td width="15%"><b style="color:red">Medium</b></td></td> </tr> <tr> <td></td> <td></tr></td> </tr> <tr> <td></td> <td><tr id="vir2" style="display:none;"></td> </tr> <tr> <td></td> <td><td><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>Trojan Horse IRC/Backdoor.SdBot4.FRV</b></td></td> </tr> <tr> <td></td> <td><td>Virus</td></td> </tr> <tr> <td></td> <td><td><b style="color:red">Medium</b></td></td> </tr> <tr> <td></td> <td></td> </tr> <tr> <td></td> <td></tr></td> </tr> <tr> <td></td> <td><tr id="vir3" style="display:none;"></td> </tr> <tr> <td></td> <td><td><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>W95/Elkern F-Secure</b></td></td> </tr> <tr> <td></td> <td><td>Virus</td></td> </tr> <tr> <td></td> <td><td><b style="color:red">High</b></td></td> </tr> <tr> <td></td> <td></tr></td> </tr> <tr> <td></td> <td><tr id="vir4" style="display:none;"></td> </tr> <tr> <td></td> <td></td> </tr> <tr> <td></td> <td><td><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>AdvWare.Hotbar</b></td></td> </tr> <tr> <td></td> <td><td>Virus</td></td> </tr> <tr> <td></td> <td><td><b style="color:red">High</b></td></td> </tr> <tr> <td></td> <td></tr></td> </tr> <tr> <td></td> <td><tr id="vir5" style="display:none;"></td> </tr> <tr> <td></td> <td><td><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>W95/Elkern F-Secure</b></td></td> </tr> <tr> <td></td> <td></td> </tr> <tr> <td></td> <td><td>Virus</td></td> </tr> <tr> <td></td> <td><td><b style="color:red">High</b></td></td> </tr> <tr> <td></td> <td></tr></td> </tr> <tr> <td></td> <td><tr id="vir6" style="display:none;"></td> </tr> <tr> <td></td> <td><td><img src="<a href="http://scan91.frelossa.cz.cc/images/8f3xcu.gif" target="_blank">/images/8f3xcu.gif</a>" align="top"> <b>Trojan Horse Generic11.OQJ</b></td></td> </tr> <tr> <td></td> <td><td>Virus</td></td> </tr> </tbody> </table>